Welcome to your CompTIA CySA+ Certification exam ( 1 )
1-) A security analyst has observed several incidents within an organization that are affecting one specific piece of hardware on the network. Further investigation reveals the equipment vendor previously released a patch. Which of the following is the MOST appropriate threat classification for these incidents?
2-) An organization's network administrator uncovered a rogue device on the network that is emulating the charactenstics of a switch. The device is trunking protocols and inserting tagging va the flow of traffic at the data link layer Which of the following BEST describes this attack?
3-) A security analyst is required to stay current with the most recent threat data and intelligence reports. When gathering data, it is MOST important for the data to be:
4-) A security analyst is performing a Diamond Model analysis of an incident the company had last quarter. A potential benefit of this activity is that it can identify:
5-) A custom script currently monitors real-time logs of a SAMIL authentication server to mitigate brute-force attacks. Which of the following is a concern when moving authentication to a cloud service?
6-) A threat intelligence analyst has received multiple reports that are suspected to be about the same advanced persistent threat. To which of the following steps in the intelligence cycle would this map?
7-) An analyst is working with a network engineer to resolve a vulnerability that was found in a piece of legacy hardware, which is critical to the operation of the organization's production line. The legacy hardware does not have third-party support, and the OEM manufacturer of the controller is no longer in operation. The analyst documents the activities and verifies these actions prevent remote exploitation of the vulnerability. Which of the following would be the MOST appropriate to remediate the controller?
😎 Which of the following technologies can be used to house the entropy keys for task encryption on desktops and laptops?
9-) Which of the following is the use of tools to simulate the ability for an attacker to gain access to a specified network?
10-) A security analyst is reviewing the following log entries to identify anomalous activity:
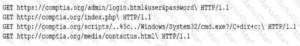
Which of the following attack types is occurring?
11-) Massivelog log has grown to 40GB on a Windows server At this size, local tools are unable to read the file, and it cannot be moved off the virtual server where it is located. Which of the following lines of PowerShell script will allow a user to extract the last 10.000 lines of the loq for review?
12-) A Chief Security Officer (CSO) is working on the communication requirements (or an organization's incident response plan. In addition to technical response activities, which of the following is the main reason why communication must be addressed in an effective incident response program?
13-) Which of the following assessment methods should be used to analyze how specialized software performs during heavy loads?
14-) An organization that uses SPF has been notified emails sent via its authorized third-party partner are getting rejected A security analyst reviews the DNS entry and sees the following: v=spf1 ip4:180.10.6.5 ip4:180.10.6.10 include:robustmail.com –all The organization's primary mail server IP is 180.10 6.6, and the secondary mail server IP is 180.10.6.5. The organization's third-party mail provider is "Robust Mail" with the domain name robustmail.com. Which of the following is the MOST likely reason for the rejected emails?
15-) A cybersecurity analyst needs to determine whether a large file named access log from a web server contains the following loC: ../../../../bin/bash Which of the following commands can be used to determine if the string is present in the log?
16-) A security analyst discovers accounts in sensitive SaaS-based systems are not being removed in a timely manner when an employee leaves the organization To BEST resolve the issue, the organization should implement
17-) A security analyst is supporting an embedded software team. Which of the following is the BEST recommendation to ensure proper error handling at runtime?
18-) A security analyst receives an alert that highly sensitive information has left the company's network Upon investigation, the analyst discovers an outside IP range has had connections from three servers more than 100 times m the past month The affected servers are virtual machines Which of the following is the BEST course of action?
19-)An organization has not had an incident for several month. The Chief information Security Officer (CISO) wants to move to proactive stance for security investigations. Which of the following would BEST meet that goal?
20-) A security analyst needs to reduce the overall attack surface. Which of the following infrastructure changes should the analyst recommend?