
What is a Network and Why is it Important in the World of Technology?
What is a network and why is it important in the world of technology?

Two or more computers that are linked in order to share resources (such as printers and CDs), exchange files, or allow electronic communications.
Advantages of using networks over standalone computers:
• Networks enable multiple users to share the network’s resources
(devices and data)
• Networks allow you to manage, or administer, resources on multiple
computers from a central location
What is the OSI model and what is its purpose?
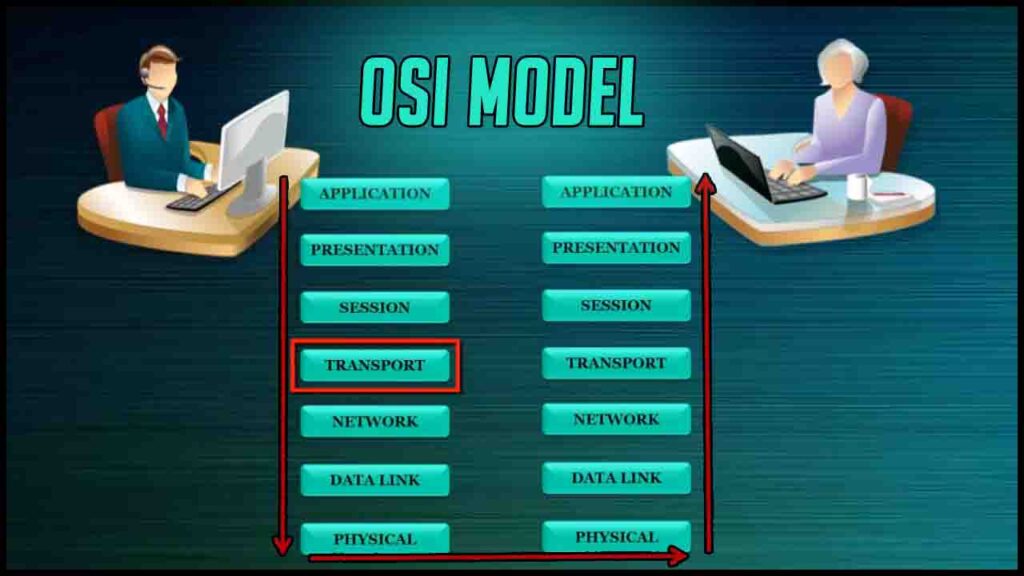
The open systems interconnection (OSI) model provides a standard for different computer systems to be able to communicate with each other.
The OSI Model can be seen as a universal language for computer networking. It is based on the concept of splitting up a communication system into seven abstract layers, each one stacked upon the last.
Purposes of the OSI Model are:
-To standardize data networking protocols to allow communication between all networking devices across the entire planet.
-To create a common platform for software developers and hardware manufactures that encourage the creation of networking products that can communicate with each other over the network.
-To help network administrators by dividing large data exchange process into smaller segments. Smaller segments are easier to understand, manage and troubleshoot.
What is a protocol and what role do they play in networking?
In networking, a protocol is a set of rules for formatting and processing data. Network protocols are like a common language for computers. Protocol role the computers within a network may use vastly different software and hardware; however, the use of protocols enables them to communicate with each other regardless
What is a LAN, WAN, and MAN?
• Local area network (LAN): confined to a relatively small space, such as a building or an office
• Metropolitan area network (MAN): larger than a LAN; connects clients and servers from multiple buildings
• Wide area network (WAN): connects two or more geographically distinct LANs or MANs
What is the difference between a router, switch, and hub?
A router, switch, and hub are all networking devices that allow multiple devices to connect to a network. However, they differ in how they handle network traffic and how they direct data packets.
• Hubs are “dumb” devices that pass on anything received on one connection to all other connections.
• Switches are semi-intelligent devices that learn which devices are on which connection. ‘
• Routers are essentially small computers that perform a variety of intelligent tasks.
What is an IP address and how is it used in networking?
An IP address is a unique numerical identifier assigned to every device that is connected to a network. IP stands for “Internet Protocol”, and the address is used to identify and communicate with devices on a network.
In computer networking, the Internet Protocol (IP) is used to route packets of data between devices. An IP address is required to route these packets of data to the correct destination device. The IP address is used in the following ways in networking:
-Identification: IP addresses uniquely identify devices on a network. This allows other devices on the network to communicate with them.
–Addressing: IP addresses are used to specify the source and destination of data packets as they move through a network.
–Routing: IP addresses are used to route data packets between networks. Routers use the destination IP address to determine the next hop on the path to the packet’s destination.
There are two versions of IP addresses currently in use: IPv4 and IPv6. IPv4 uses a 32-bit address, which limits the number of unique addresses to approximately 4 billion. IPv6 uses a 128-bit address, which allows for an enormous number of unique addresses. IPv6 is gradually replacing IPv4 due to the increasing number of devices that require unique IP addresses.
What is the difference between IPv4 and IPv6?
| IPv4 | IPV6 |
| IPv4 has a 32-bit address length | IPv6 has a 128-bit address length |
| It Supports Manual and DHCP address configuration | It supports Auto and renumbering address configuration |
| In IPv4 end to end, connection integrity is Unachievable | In IPv6 end to end, connection integrity is Achievable |
What is a subnet mask and how is it used in networking?
A subnet mask defines the range of IP addresses that can be used within a network or subnet. It also separates an IP address into two parts: network bits and host bits.
Subnet masks are used when subnetting, which is when you break a network up into smaller networks. By adjusting the subnet mask, you can set the number of available IP addresses within a network.
What is a default gateway and how does it work?
A default gateway is a network device that serves as an access point for traffic leaving one network and entering another network. It is usually a router, although it can also be a layer 3 switch or other networking device.
The default gateway is used to route traffic from a device on a local network to devices on other networks or the internet. When a device on a local network wants to communicate with a device on another network, it sends the traffic to the default gateway. The default gateway then routes the traffic to the appropriate destination network.
For example, if you have a home network with a router as the default gateway and you want to browse a website on the internet, your computer sends the request to the router. The router then routes the traffic to the internet, and the website responds by sending the data back to the router, which then forwards the data back to your computer.
The default gateway is typically set on each device on a network, including computers, servers, and other devices. It is usually set to the IP address of the router or other networking device that serves as the default gateway for the network.
What is DHCP and how does it work?
DHCP is a client-server protocol in which servers manage a pool of unique IP addresses, as well as information about client configuration parameters. The servers then assign addresses out of those address pools. DHCP-enabled
clients send a request to the DHCP server whenever they connect to a network.
When a device connects to a network that uses DHCP, it sends a broadcast message requesting an IP address and other network configuration information. A DHCP server on the network receives this request and responds with an offer of an available IP address, along with other configuration information such as subnet mask, default gateway, and DNS server addresses.
If the device accepts the offer, it sends a request to the DHCP server to request the offered IP address. The DHCP server then sends a message to the device acknowledging that the IP address has been assigned, and providing the other configuration information.
The DHCP server typically assigns an IP address to the device for a limited period of time, called a lease. When the lease expires, the device must request a new IP address, which may or may not be the same as the previous one.
DHCP allows network administrators to easily manage IP address allocation and other network configuration information, such as subnet masks, default gateways, and DNS server addresses. It also makes it easier to reconfigure a network by enabling administrators to centrally manage IP address ranges and other network settings.
What is DNS and how does it work?
The Domain Name System (DNS) turns domain names into IP addresses, which browsers use to load internet pages. Every device connected to the internet has its own IP address, which is used by other devices to locate the device. DNS servers make it possible for people to input normal words into their browsers, such as Fortinet.com, without having to keep track of the IP address for every website.
In a usual DNS query, the URL typed in by the user has to go through four servers for the IP address to be provided. The four servers work with each other to get the correct IP address to the client, and they include:
- DNS recursor: The DNS recursor, which is also referred to as a DNS resolver, receives the query from the DNS client. Then it communicates with other DNS servers to find the right IP address. After the resolver retrieves the request from the client, the resolver acts like a client itself. As it does this, it makes queries that get sent to the other three DNS servers: root nameservers, top-level domain (TLD) nameservers, and authoritative nameservers.
- Root nameservers: The root nameserver is designated for the internet’s DNS root zone. Its job is to answer requests sent to it for records in the root zone. It answers requests by sending back a list of the authoritative nameservers that go with the correct TLD.
- TLD nameservers: A TLD nameserver keeps the IP address of the second-level domain contained within the TLD name. It then releases the website’s IP address and sends the query to the domain’s nameserver.
- Authoritative nameservers: An authoritative nameserver is what gives you the real answer to your DNS query. There are two types of authoritative nameservers: a master server or primary nameserver and a slave server or secondary nameserver. The master server keeps the original copies of the zone records, while the slave server is an exact copy of the master server. It shares the DNS server load and acts as a backup if the master server fails.
What is a firewall and how does it work?
Firewalls prevent unauthorized access to networks through software or firmware. By utilizing a set of rules, the firewall examines and blocks incoming and outgoing traffic.
Fencing your property protects your house and keeps trespassers at bay; similarly, firewalls are used to secure a computer network. Firewalls are network security systems that prevent unauthorized access to a network. It can be a hardware or software unit that filters the incoming and outgoing traffic within a private network, according to a set of rules to spot and prevent cyberattacks.
Firewalls are used in enterprise and personal settings. They are a vital component of network security. Most operating systems have a basic built-in firewall. However, using a third-party firewall application provides better protection
How does it work ?
Firewalls filter the network traffic within a private network. It analyses which traffic should be allowed or restricted based on a set of rules. Think of the firewall like a gatekeeper at your computer’s entry point which only allows trusted sources, or IP addresses, to enter your network.
A firewall welcomes only those incoming traffic that has been configured to accept. It distinguishes between good and malicious traffic and either allows or blocks specific data packets on pre-established security rules.
These rules are based on several aspects indicated by the packet data, like their source, destination, content, and so on. They block traffic coming from suspicious sources to prevent cyberattacks.
What is VPN and why is it used in networking?
A Virtual Private Network (VPN) adds security and anonymity to users when they connect to web-based services and sites. A VPN hides the user’s actual public IP address and “tunnels” traffic between the user’s device and the remote server. Most users sign up for a VPN service online anonymity to avoid being tracked, and they often use public Wi-Fi where increased risks threaten the safety of their data.
Why Do I Need a VPN?
When you make a connection to a web server, your browser performs a lookup on the domain name from Domain Name Services (DNS) servers, gets the IP address, and then connects to the server. In most cases, the connection is encrypted using SSL/TLS. Even with SSL/TLS, numerous attacks on public Wi-Fi are possible. For example, a clever attacker can perform a downgrade on the version of TLS used to encrypt data, making communication vulnerable to brute force.
With a VPN added to the connection, the VPN service packages data in its own encryption and sends it across the network. The targeted server sees the VPN’s public IP address instead of the user’s public IP address. Should an attacker hijack the connection and eavesdrop on data, good VPN encryption eliminates the possibility of a brute force opportunity, which discloses data in a cryptographically insecure connection.
How to Use a VPN
The first step in VPN setup is finding a provider that’s right for you. Several VPN providers are available, but each one has its pros and cons. For example, you need a provider with a protocol that all devices support. It should be easy to set up, available from any geolocation, and provide cryptographically secure encryption for adequate security in public Wi-Fi use.
A main differentiating factor between a good VPN and one that offers little advantages is the number of users on a single IP address. Some service providers block VPN IP addresses because spammers and malicious threat actors also use VPN to anonymize their connection. Service providers can download a list of VPN IP addresses and block them from accessing local services. Good VPN offers private IP addresses, which costs more but also offers increased freedom and anonymity on the Internet.
After you choose a VPN, you then must configure your device to use it. These configurations are specific to each VPN provider, so yours equip you with their step-by-step instructions. Some VPN providers give you an install file to help with the setup process, which is helpful if you are unfamiliar with operating-system configurations.
What is NAT and how is it used in networking?
Network Address Translation (NAT) is a process that enables one, unique IP address to represent an entire group of computers. In network address translation, a network device, often a router or NAT firewall, assigns a computer or computers inside a private network a public address. In this way, network address translation allows the single device to act as an intermediary or agent between the local, private network and the public network that is the internet. NAT’s main purpose is to conserve the number of public IP addresses in use, for both security and economic goals.
Network Address Translation FAQs
What is Network Address Translation?
Network Address Translation (NAT) conserves IP addresses by enabling private IP networks using unregistered IP addresses to go online. Before NAT forwards packets between the networks it connects, it translates the private internal network addresses into legal, globally unique addresses.
NAT configurations can reveal just one IP address for an entire network to the outside world as part of this capability, effectively hiding the entire internal network and providing additional security. Network address translation is typically implemented in remote-access environments, as it offers the dual functions of address conservation and enhanced security.
What is a MAC address and how is it used in networking?
Media Access Control (MAC) Address –
MAC Addresses are the unique 48-bits hardware number of a computer, which is embedded into a network card (known as a Network Interface Card) during the time of manufacturing. MAC Address is also known as the Physical Address of a network device. In IEEE 802 standard, Data Link Layer is divided into two sublayers –
Logical Link Control(LLC) Sublayer
Media Access Control(MAC) Sublayer
MAC address is used by the Media Access Control (MAC) sublayer of the Data-Link Layer. MAC Address is worldwide unique since millions of network devices exist and we need to uniquely identify each.
What is QoS and how does it work?
QoS or Quality of Service in networking is the process of managing network resources to reduce packet loss as well as lower network jitter and latency. QoS technology can manage resources by assigning the various types of network data different priority levels.
QoS is usually applied on networks that cater to traffic that carry resource-intensive data like:
- Video-on-demand
- Voice over IP (VoIP)
- Internet Protocol television (IPTV)
- Streamed media
- Video conferencing
- Online gaming
These sorts of data need to be transmitted in the shortest amount of time to be consumable at the receiving end.
Understanding Network QoS
To make things a bit clearer, let us take a real-world example of a traffic jam on a highway at rush hour. All the drivers sitting in the middle of the jam have one plan – make it to their final destinations. And so, at snail’s pace, they keep moving along.
Then the sound of an ambulance’s siren alerts them to a vehicle that needs to get to its destination more urgently – and ahead of them. And so, the drivers move out of what now becomes the ambulance’s “priority queue”, and let it pass.
Similarly, when a network transports data, it too has a setup where some sort of data is treated preferably over all the others. The packets of important data need to reach their destinations much quicker than the rest of them because they are time-sensitive and will “expire” if they don’t make it on time.
What is a VLAN and how is it used in networking?
A VLAN (Virtual Local Area Network) is a type of network segmentation technology that allows network administrators to create virtual networks that are isolated from each other, even though they may be physically connected to the same network infrastructure.
In traditional network design, all devices connected to the same network share the same broadcast domain, which can lead to inefficient use of network resources, security concerns, and difficulties in network management. By implementing VLANs, a network administrator can divide a physical network into multiple logical networks, each with its own broadcast domain.
VLANs work by grouping devices based on certain criteria, such as their location, department, or function, and then assigning them to a virtual network. This is typically done at the switch level, by creating virtual LANs and associating them with specific switch ports. Devices connected to those ports then become part of the virtual LAN.
VLANs are used in networking to improve network efficiency, security, and flexibility. By isolating network traffic to specific groups of devices, VLANs can reduce the amount of broadcast traffic and increase network bandwidth. They can also improve network security by limiting access to resources to only authorized devices, and they can simplify network management by allowing administrators to manage multiple logical networks as if they were separate physical networks.
What is a port and how does it work?
In computer networking, a port is a communication endpoint that enables a device to send and receive data over a network. Ports are identified by unique numbers, called port numbers, and are used to direct network traffic to specific applications or services running on a device.
Port numbers are divided into three ranges: well-known ports (0-1023), registered ports (1024-49151), and dynamic or private ports (49152-65535). Well-known ports are typically reserved for standard services, such as HTTP (port 80), FTP (port 21), and SMTP (port 25). Registered ports are assigned to specific applications or services by the Internet Assigned Numbers Authority (IANA), and dynamic or private ports are used for temporary connections.
When a device initiates a network connection to another device, it specifies both the IP address of the destination device and the port number of the application or service that it wants to communicate with. The receiving device uses the port number to direct the incoming traffic to the appropriate application or service.
For example, if a user types a URL into their web browser to access a website, the browser sends a request to the web server’s IP address using port 80 (or sometimes port 443 for secure connections). The web server receives the request and directs it to the appropriate web server software, which then generates a response that is sent back to the user’s web browser using the same port number.
What is packet loss and how can it be prevented?
Packet loss is a network issue that occurs when one or more packets of data fail to reach their destination. This can happen for a variety of reasons, such as network congestion, faulty network hardware, or network errors.
Packet loss can cause a range of problems, including poor network performance, slow internet speeds, and distorted or incomplete data. In some cases, it can even lead to service disruptions or application failures.
There are several ways to prevent packet loss, depending on the underlying cause. Here are some common methods:
Monitor network performance: One way to prevent packet loss is to monitor network performance and identify potential issues before they become major problems. This can be done using network monitoring tools that analyze network traffic and identify bottlenecks or congestion points.
Improve network hardware: Another way to prevent packet loss is to upgrade or replace faulty network hardware, such as switches, routers, or cables. This can help to ensure that data packets are transmitted reliably and efficiently across the network.
Optimize network traffic: Network congestion can be a major cause of packet loss. To prevent this, network administrators can optimize network traffic by limiting bandwidth usage, prioritizing traffic based on importance, or using Quality of Service (QoS) policies to ensure that critical traffic is given priority over less important traffic.
Use error detection and correction techniques: To prevent packet loss due to network errors, error detection and correction techniques such as checksums and retransmission can be used. These techniques help to ensure that data is transmitted accurately and that any errors are corrected in real-time.
In summary, packet loss is a common network issue that can cause poor network performance, slow internet speeds, and other problems. To prevent packet loss, network administrators can monitor network performance, improve network hardware, optimize network traffic, and use error detection and correction techniques. By taking these steps, network administrators can help to ensure that data packets are transmitted reliably and efficiently across the network.
What is a ping and how is it used in networking?
In computer networking, “ping” is a tool used to test the connectivity between two devices on a network. It works by sending an Internet Control Message Protocol (ICMP) packet from one device to another and measuring the time it takes for the packet to travel from the source device to the destination device and back.
